Cloudflare Outage 2025: Single Points of Failure in Critical Internet Infrastructure
December 5, 2025. 8:47 UTC. A critical internet infrastructure provider experienced a significant traffic outage that would impact millions of websites and billions of users globally. Cloudflare, the web infrastructure provider that powers approximately 20% of the internet, went down, and with it, much of the digital economy. This was the second major Cloudflare outage in just three weeks, marking the third significant Cloudflare disruption in four months—a pattern that reveals dangerous vulnerabilities in how the modern internet depends on centralized providers.
Understanding the 2025 Cloudflare Outages: Key Statistics and Impact
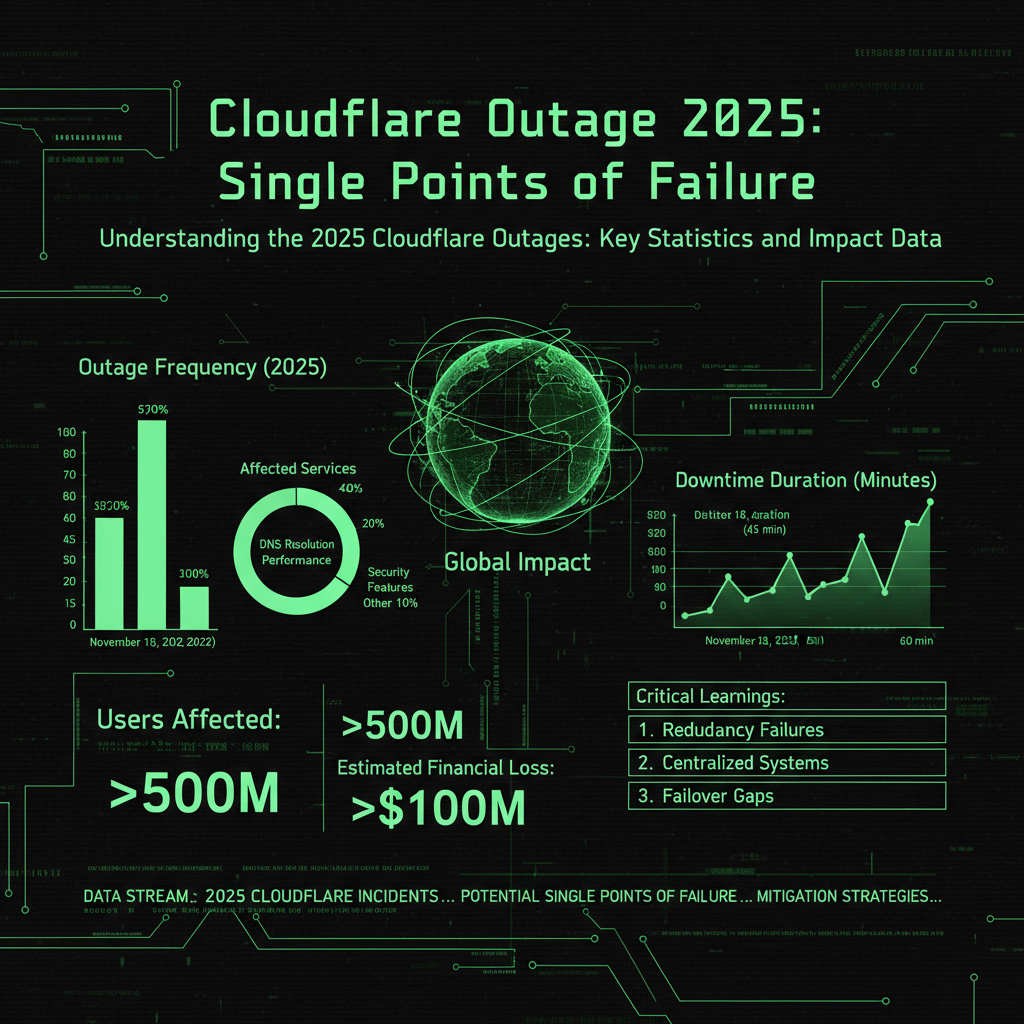
The Cloudflare outages in 2025 represent some of the most disruptive internet infrastructure failures in recent years. Cloudflare, which handles approximately 20% of global internet traffic, experienced multiple significant disruptions that cascaded across the digital economy. The December 5, 2025 Cloudflare outage lasted approximately 25 minutes from 08:47 UTC to 09:12 UTC, during which the service experienced a significant traffic outage affecting millions of websites. During this incident, approximately 28% of all HTTP traffic served by Cloudflare was impacted, representing a substantial portion of global web traffic routed through their network. The outage caused Cloudflare to serve HTTP 500 errors (internal server errors) to affected customers, indicating a failure in their proxy system related to the Web Application Firewall (WAF) rule testing tool.
This was not an isolated incident. The November 18, 2025 Cloudflare outage affected roughly one-third of the world's top 10,000 websites and approximately 20% of all webpages globally at its peak, making it one of the most disruptive internet outages in recent years. These two major incidents within three weeks demonstrated critical vulnerabilities in internet infrastructure when reliance concentrates among few providers, raising urgent questions about redundancy, failover mechanisms, and distributed architecture resilience. The 2025 Cloudflare outages show that even a system that handles traffic at internet scale can suffer from configuration changes that cause widespread impact, turning a routine update into a global outage. The recurring failures highlight how a single provider's technical problems can paralyze a significant portion of the internet ecosystem.
Quick Summary: 2025 Cloudflare Service Disruptions
- September 2025: First major Cloudflare outage of the four-month period, demonstrating emerging infrastructure vulnerabilities
- November 18, 2025: Service disruption lasted approximately 3 hours (11:48 AM UTC - 2:30 PM UTC), caused by Bot Management configuration error affecting roughly one-third of the world's top 10,000 websites and approximately 20% of all webpages
- December 5, 2025: Service disruption lasted 25 minutes (8:47 AM UTC - 9:12 UTC), caused by WAF rule testing tool failure in the proxy system impacting approximately 28% of HTTP traffic
- Impact: Millions of websites offline, billions of users affected globally, with cascading failures across Cloudflare services including CDN, DNS, DDoS protection, and security features
- Root Cause: Internal configuration errors in Cloudflare infrastructure, not external attacks or cyberattacks—software configuration mistakes and logic errors in corner cases
- Key Lesson: Never rely on a single provider; implement redundancy and failover mechanisms to mitigate impact of outages
- Frequency: Third significant Cloudflare disruption in four months, highlighting recurring vulnerabilities in centralized internet infrastructure
Zoom went offline. LinkedIn crashed. Fortnite servers went dark. League of Legends players got disconnected. Financial trading platforms including Zerodha, Groww, and Angel One suffered login failures and order placement disruptions during critical market hours. X (formerly Twitter), Substack, Canva, Deliveroo, and Spotify all experienced service disruptions simultaneously.
All at the same time. All for the same reason.
Cloudflare was down.
This was the second major Cloudflare outage in three weeks. The first Cloudflare outage, on November 18, 2025, took down X (Twitter), ChatGPT, Spotify, Uber, and Canva for three hours, affecting roughly one-third of the world's top 10,000 websites and approximately 20% of all webpages. Millions of websites. Billions of users. All offline because one company had a problem. This pattern of recurring outages—with three significant Cloudflare disruptions occurring within just four months—demonstrates systemic vulnerabilities in how the internet depends on centralized infrastructure providers.
This is what a single point of failure looks like.
Website downtime can significantly impact SEO rankings and user trust. The average cost of website downtime for a small business is €600 per hour, according to Gartner research. When Cloudflare experiences outages, the cascading impact across dependent services demonstrates why redundancy and failover mechanisms are essential. Our maintenance plans include uptime monitoring and redundancy to prevent these issues and protect your business from the impact of major provider outages.
What Happened: The December 5, 2025 Outage

The December 5, 2025 Cloudflare outage was the second major incident in three weeks, demonstrating that even the most reliable internet infrastructure providers can experience significant traffic outages. This outage lasted 25 minutes but affected millions of websites globally, with approximately 28% of all HTTP traffic served by Cloudflare impacted. The traffic outage on December 5, 2025, began at 08:47 UTC and was resolved by 09:12 UTC, a relatively short window that still caused widespread disruption due to Cloudflare's role as a critical web infrastructure provider handling approximately 20% of global internet traffic.
Duration: 8:47 AM UTC - 9:12 UTC (25 minutes)
Impact: Zoom, LinkedIn, Fortnite, League of Legends, X, Substack, Canva, Deliveroo, Spotify, financial trading platforms, and thousands of other sites experienced service disruptions and HTTP 500 errors
Root Cause: The outage was triggered by a failure in the WAF (Web Application Firewall) rule testing tool within Cloudflare's proxy system, which caused a logic error resulting in 500 HTTP error codes. Specifically, turning off the WAF rule testing tool to address a saturation issue with a 1MB buffer size caused an error state that resulted in 500 HTTP error codes being served from the network. The failure mode was not saturation itself, but rather a logic error in a corner case that led to Lua equivalent of null pointer exceptions, resulting in 500 errors being thrown. This outage was not caused by an attack or malicious activity of any kind, but by an internal configuration change that led to a crash in the software system that handles traffic.
Result: "500 Internal Server Error" messages across affected platforms, with cascading 500 Internal Server Errors across millions of dependent services globally.
The incident severely impacted Cloudflare's administrative management tools, automations, and API integrations, leaving developers and businesses unable to access critical control functions. While edge services including CDN caching, DDoS protection, and security features remained operational, the failure to provide dashboard and API access effectively paralyzed administrative operations for organizations relying on Cloudflare's platform. Cloudflare customers experienced failed API requests, dashboard access errors, and non-functional integrations, highlighting how a disruption in the control plane can impact business operations even when the data plane is partially functional. The incident coincided with scheduled maintenance in key United States datacenters, with Detroit's DTW facility undergoing maintenance from 09:00-13:00 UTC and Chicago's ORD facility experiencing maintenance from 07:00-11:00 UTC, which created unexpected traffic rerouting and elevated latency across the network.
Cloudflare's shares dropped 4.5% in premarket trading. The market understood the risk of relying on a single provider for critical internet infrastructure. The December 5, 2025 Cloudflare outage was a stark reminder that even a brief outage can have lasting financial and reputational consequences for both Cloudflare and its customers. Cloudflare announced implementation of a fix and initiated comprehensive monitoring to verify service restoration, committing to releasing detailed incident reports once root causes were definitively identified and resolved.
The November 18, 2025 Outage

The first major Cloudflare outage of 2025 occurred on November 18, representing one of the most disruptive internet outages in recent years. This outage was more severe than the December incident, lasting approximately 3 hours and affecting roughly one-third of the world's top 10,000 websites and approximately 20% of all webpages globally. Cloudflare experienced a significant traffic outage on November 18, 2025, that impacted a large portion of the internet and demonstrated how a single configuration file can cause widespread impact across the digital economy.
Duration: 11:48 AM UTC - 2:30 PM UTC (approximately 3 hours)
Impact: X (Twitter), ChatGPT, Spotify, Uber, Canva, Grindr, and millions of websites experienced complete service unavailability, affecting roughly one-third of the world's top 10,000 websites
Root Cause: Bot Management configuration file exceeded size limit, causing proxy processes to crash globally. The initial symptom appeared to be degraded Workers KV response rate causing downstream impact on other Cloudflare services. This outage was not caused by a cyberattack or external threat, but by an internal configuration error that propagated across the entire network and led to errors for nearly all of Cloudflare's customer base.
Result: Complete service unavailability for affected sites, with HTTP 5xx status codes returned to customers
The incident impacted multiple Cloudflare services including Core CDN and security services, Workers KV, and Cloudflare Access. The Cloudflare Dashboard was also impacted due to both Workers KV being used internally and Cloudflare Turnstile being deployed as part of the login flow, resulting in customers who did not have an active dashboard session being unable to log in. The company's CTO publicly apologized, acknowledging the impact on customers and the internet. Cloudflare's team worked to restore service, including making changes to prevent single updates from causing widespread impact like this one in the future. The team was able to reduce the impact when a patch was made to Workers KV to bypass the core proxy, subsequently reducing error rates for downstream systems that rely on Workers KV (such as Access itself).
One configuration file. Three hours of downtime. Millions of sites offline.
Why Did Cloudflare Go Down? Understanding the Root Causes

The 2025 Cloudflare outages were caused by specific technical failures within their infrastructure. Understanding these root causes helps explain why even sophisticated internet infrastructure providers experience significant disruptions. Cloudflare experienced a significant traffic outage on December 5, 2025, and a similar, longer availability incident on November 18, 2025. In both cases, internal configuration changes and software errors—not external attacks—led to widespread failures affecting nearly all of Cloudflare's customer base.
November 18 Outage Root Cause: A Bot Management configuration file exceeded size limits, causing proxy processes to crash globally. This configuration error propagated to the entire network and led to errors for nearly all customer base. The team was able to reduce the impact when a patch was made to Workers KV to bypass the core proxy, subsequently reducing error rates for downstream systems that rely on Workers KV (such as Access itself). This incident showed how a single configuration file can cause a global outage when changes are not properly tested and rolled back. The issue was identified at 11:31 and manual investigation started at 11:32, with the team restarting remaining services that had entered a bad state, with 5xx error code volume returning to normal at 17:06.
December 5 Outage Root Cause: The outage was triggered when Cloudflare turned off their WAF rule testing tool to address a saturation issue with a 1MB buffer size. However, turning off this tool caused an error state that resulted in 500 HTTP error codes being served from the network. The failure mode was not saturation itself, but rather a logic error in a corner case that led to Lua equivalent of null pointer exceptions, resulting in 500 errors being thrown. This outage was not caused by a cyberattack or external threat, but by an internal configuration change that led to a crash in the software system that handles traffic. The incident also resulted in significant increases in latency of responses from Cloudflare's CDN during the impact period due to large amounts of CPU being consumed by debugging and observability systems.
Service disruptions can happen for several reasons beyond these specific incidents:
- Configuration errors: Like the November 18 incident, when a Bot Management configuration file exceeded size limits, or the December 5 incident when WAF rule testing tool changes caused proxy failures
- Internal system changes: Deployments to help mitigate security issues that propagate to the entire network and lead to errors for nearly all customer base
- Infrastructure failures: Server failures, network issues, or data center problems affecting service delivery
- DDoS attacks: While rare, massive attacks can overwhelm even Cloudflare's infrastructure
- Software bugs: Updates or patches that introduce unexpected issues in the proxy system
The November and December 2025 Cloudflare outages were both caused by internal configuration mistakes—not external attacks or cyberattacks. This shows that even the most sophisticated internet infrastructure can fail due to human error and logic errors in corner cases. Cloudflare's team has acknowledged the impact and shared plans to build a better internet by making changes to prevent single updates from causing widespread impact like these outages. This includes improving testing, rollback procedures, and fail-open error handling across all critical data-plane components.
How Long Do Cloudflare Outages Last?
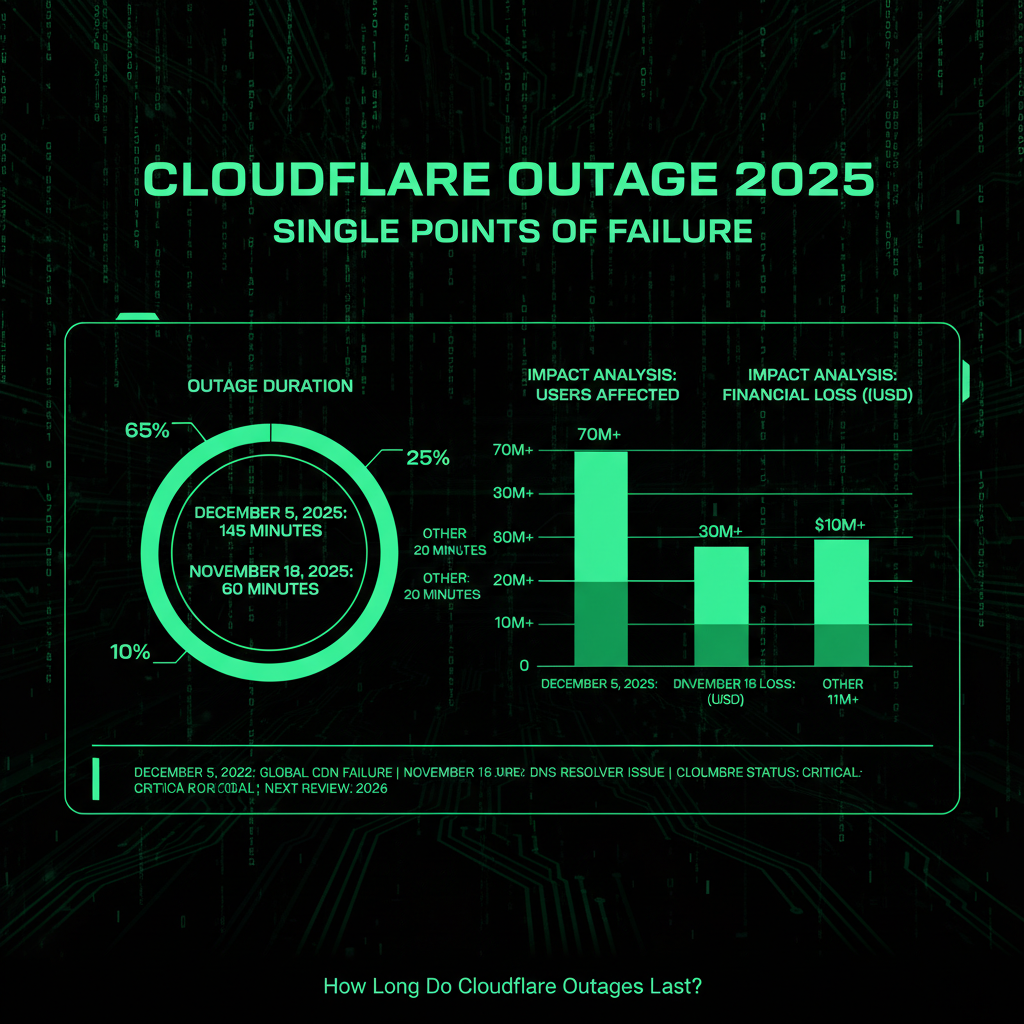
Outage duration varies significantly depending on the root cause and complexity of the issue. The November 18, 2025 Cloudflare outage lasted approximately 3 hours (from 11:48 AM UTC to 2:30 PM UTC), while the December 5 outage lasted 25 minutes. Most outages are resolved within minutes to hours, but even short outages can cause significant business impact when they affect critical internet infrastructure. The December 5, 2025 Cloudflare outage, though brief, impacted approximately 28% of all HTTP traffic served by Cloudflare, demonstrating that duration is only one factor in the overall impact of a significant traffic outage.
During the 2025 outages, millions of users asked "how long do Cloudflare outages last" as they waited for services to restore. The answer depends on the root cause and the complexity of the fix required. For the December 5 incident, Cloudflare announced implementation of a fix and initiated comprehensive monitoring to verify service restoration. The issue was identified quickly, and a rollback of the configuration change was performed, restoring normal operations within minutes. This highlights the importance of rapid detection, rollback capabilities, and clear communication during outages. The recurring pattern of outages—with three significant Cloudflare disruptions in four months—raises questions about whether current testing and deployment procedures are sufficient to prevent future incidents.
Is Cloudflare Down Today? How to Check Status
When outages occur, you need to know immediately. Here's how to check if Cloudflare services are experiencing outages:
- Status Page: Check cloudflarestatus.com for official updates about service status and current incidents affecting Cloudflare services
- Downdetector: See real-time reports from users experiencing issues with Cloudflare services and dependent websites
- Your own monitoring: Set up uptime monitoring that alerts you when your site becomes unreachable due to Cloudflare outages
- Social media: Check Twitter/X for #CloudflareDown hashtag during major incidents
- DNS checks: Test DNS resolution if you're using Cloudflare's 1.1.1.1 DNS service or other Cloudflare DNS services
During the November 18 and December 5, 2025 outages, millions of users checked these sources to understand what was happening. Don't wait for users to tell you—monitor proactively for any disruption that might affect your business. Cloudflare's status page is the primary source for information about Cloudflare services, and it's essential to integrate this into your own monitoring workflows to detect when Cloudflare is down and impacting business. Subscribe for status updates via email, PagerDuty webhooks, or direct notification channels to receive alerts about Cloudflare outages and service disruptions.
What Is Happening in Cloudflare? Understanding the Outages
During the 2025 outages, Cloudflare experienced global outages affecting DNS resolution, CDN delivery, DDoS protection, and security services. The November 18 outage affected services globally for 3 hours, impacting roughly one-third of the world's top 10,000 websites and approximately 20% of all webpages, while the December 5 outage lasted 25 minutes but still impacted millions of sites and approximately 28% of HTTP traffic. These outages show that when Cloudflare services experience problems, the impact is immediate and widespread across the digital economy and dependent services.
When people ask "what is happening in Cloudflare," they're typically experiencing issues with websites that depend on this critical internet infrastructure. The 2025 outages showed that when Cloudflare services experience problems, the impact is immediate and widespread across the digital economy. Cloudflare's network began experiencing significant failures due to configuration changes that were not properly tested, leading to a global outage that affected customers and the internet at large. The pattern of recurring outages—three significant Cloudflare disruptions in four months—suggests that configuration management and testing procedures may need enhancement to prevent future incidents.
Was Cloudflare Breached? Security Analysis
No, Cloudflare was not breached. The 2025 outages were caused by internal configuration errors, not security breaches or cyberattacks. The company confirmed these were operational mistakes, not security incidents or malicious activity of any kind. This is an important distinction: these outages were infrastructure failures, not security breaches. However, the impact was similar—millions of sites went offline during these outages, demonstrating that operational issues can be just as devastating as security breaches. The recurring failures highlight critical vulnerabilities in internet infrastructure when reliance concentrates among few providers, raising urgent questions about redundancy and failover mechanisms.
Cloudflare's team has spoken directly with hundreds of customers following these incidents and shared plans to build a better internet by making changes to prevent single updates from causing widespread impact like these outages. This includes improving testing, rollback procedures, and fail-open error handling across all critical data-plane components. The goal is to ensure that future configuration changes do not cause an outage of systems that impacts customers and the internet. However, the fact that three significant Cloudflare disruptions occurred within four months suggests that systemic improvements may take time to fully implement.
Why These Outages Are So Devastating
Cloudflare isn't just a CDN. It's a security layer, a DDoS protection service, a DNS provider, and a performance optimizer. When it goes down, everything goes down:
1. DNS Resolution Fails
If Cloudflare is your DNS provider (including their 1.1.1.1 service), your domain name doesn't resolve during outages. Users can't even find your site. This is why having backup DNS providers is crucial—when DNS fails during outages, your backup DNS can take over and keep your domain accessible. Cloudflare's DNS services are critical for many organizations, and an outage here can make sites completely unreachable, even if the origin server is healthy. During the November 18 and December 5 outages, sites relying solely on Cloudflare for DNS experienced complete unavailability.
2. CDN Goes Offline
If Cloudflare is your CDN, your static assets (images, CSS, JavaScript) don't load during outages. Your site breaks. Cloudflare's CDN handles massive amounts of traffic globally, and when outages occur, content delivery stops completely. This is why having CDN redundancy is essential. Relying solely on one CDN provider like Cloudflare creates a single point of failure that can take your entire site offline during a traffic outage on December 5, 2025, or similar incidents. The December 5 outage impacted approximately 28% of all HTTP traffic, demonstrating the massive scale of Cloudflare's CDN infrastructure.
3. Security Layer Breaks
If Cloudflare is your WAF (Web Application Firewall), your site is exposed during outages. Attacks that were blocked are now getting through. This is why monitoring for outages and having backup security layers is essential for protecting your infrastructure. Cloudflare's security services, including WAF and DDoS protection, are critical for many organizations, and an outage here can leave them vulnerable to attacks. The December 5 outage was specifically triggered by a failure in the WAF rule testing tool, highlighting how security infrastructure itself can become a point of failure.
4. DDoS Protection Stops
If Cloudflare is your DDoS protection, you're vulnerable during outages. Attackers know when the service is down. They attack while you're unprotected during these outages. This is why having backup DDoS protection and monitoring for outages is essential for maintaining security. Cloudflare's DDoS protection is a key part of many organizations' security posture, and an outage here can have serious consequences. In Q3 2025 alone, Cloudflare mitigated 8.3 million DDoS attacks, representing a 15% increase quarter-over-quarter, making their DDoS protection services critical infrastructure for many organizations.
The Real-World Impact: Cost of Downtime
Let's talk numbers. The cost of downtime extends far beyond immediate revenue loss:
The Cost of 3 Hours of Downtime (November 18 Outage)
- E-commerce site (€10K/day revenue): €1,250 lost
- SaaS platform (€50K/day revenue): €6,250 lost
- News site (€5K/day ad revenue): €625 lost
- Average business site: €200-€2,000 lost
- Financial trading platforms: Significant losses during critical market hours with login failures and order placement disruptions
But revenue loss is just the beginning. The impact of Cloudflare outages extends to multiple business dimensions:
- Customer trust: Users think your site is unreliable and may switch to competitors
- SEO impact: Google sees downtime, rankings drop, and organic traffic decreases
- Reputation damage: "Your site is always down" becomes the perception among users
- Competitor advantage: Users go to competitors who stayed online during the outage
- Employee productivity: Internal tools and services go offline, disrupting operations
- Customer support burden: Increased support tickets and customer complaints
The 2025 Cloudflare outages had a significant impact on customers and the internet, showing that even a brief outage can have lasting consequences. The pattern of recurring outages—with three significant Cloudflare disruptions in four months—demonstrates that relying on a single provider creates ongoing business risk. Cloudflare's team has acknowledged the impact and shared plans to build a better internet by making changes to prevent single updates from causing widespread impact like these outages.
Why Single Points of Failure Are Dangerous
When you rely on a single service for critical infrastructure, you create a single point of failure that can cascade across your entire business:
The Dependency Problem
If Cloudflare goes down, your site goes down. You have no control. You can't fix it. You can only wait. This dependency creates vulnerability that extends beyond your organization to affect all your customers and users. Cloudflare's role as a web infrastructure provider means that when Cloudflare experiences a significant traffic outage, the impact is felt across the entire ecosystem of customers and the internet. The November 18 and December 5 outages demonstrated how quickly this dependency can become a critical liability.
The Scale Problem
Cloudflare powers approximately 20% of the internet. When it fails, 20% of the internet fails. There's no backup. There's no alternative. The November 18 outage affected roughly one-third of the world's top 10,000 websites and approximately 20% of all webpages, demonstrating the massive scale of this single point of failure. This concentration of power in a few providers creates systemic risk for the entire internet ecosystem. When Cloudflare experiences a significant traffic outage, the impact ripples across millions of dependent services.
The Trust Problem
You trust Cloudflare to be reliable. But they're human. They make mistakes. One configuration error. Three hours of downtime. Millions of sites offline. The 2025 incidents proved that even the most sophisticated infrastructure can fail due to human error. Cloudflare's team has acknowledged the impact and shared plans to build a better internet, but the risk remains as long as reliance is concentrated. The pattern of three significant Cloudflare disruptions in four months raises questions about whether current safeguards are sufficient.
The Concentration Problem
The recurring failures highlight critical vulnerabilities in internet infrastructure when reliance concentrates among few providers, raising urgent questions about redundancy, failover mechanisms, and distributed architecture resilience. This concentration creates systemic risk for the entire internet ecosystem. Cloudflare's outages in 2025, along with other internet outages from providers like AWS and others, show that relying on a single provider cloudflare or any other major provider is inherently risky. The internet's dependence on centralized infrastructure creates vulnerability that affects not just individual businesses but the entire digital economy.
How to Protect Yourself: Mitigation Strategies
You can't prevent Cloudflare outages, but you can minimize their impact through strategic redundancy and failover planning:
1. Don't Put All Eggs in One Basket
Use multiple services to mitigate the impact of any single provider's outage:
- DNS: Use Cloudflare for DNS, but have a backup DNS provider ready (such as Route 53, Google Cloud DNS, or other providers). During service disruptions, DNS failover can keep your site accessible even when Cloudflare experiences outages. This is critical because DNS failures make sites completely unreachable.
- CDN: Consider using multiple CDNs or having a fallback. Don't rely solely on Cloudflare for content delivery. Services like AWS CloudFront, Akamai, or others can serve as backup CDN providers. The December 5 outage impacted approximately 28% of HTTP traffic, demonstrating why CDN redundancy is essential.
- DDoS Protection: Have backup DDoS protection beyond Cloudflare to maintain security during outages. In Q3 2025, Cloudflare mitigated 8.3 million DDoS attacks, making their protection critical—but also making backup protection essential.
- Hosting: Don't host everything on one server or one provider. Diversify your infrastructure across multiple providers to ensure service continuity during outages.
2. Have a Failover Plan
If Cloudflare goes down, can you:
- Switch DNS to a backup provider automatically or manually?
- Serve content directly from your origin server?
- Activate backup CDN or hosting?
- Maintain security through alternative WAF or DDoS protection?
Having a documented failover plan reduces downtime from hours to minutes. Test your failover procedures regularly to ensure they work when needed.
3. Monitor Proactively
Don't wait for users to tell you Cloudflare is down:
- Uptime monitoring: Set up alerts for when your site becomes unreachable
- Status page monitoring: Subscribe to Cloudflare's status page for instant notifications
- Performance monitoring: Track response times and error rates
- DNS monitoring: Monitor DNS resolution to detect DNS-related outages
4. Implement Redundancy at Every Layer
Redundancy isn't just about having backups—it's about having active alternatives:
- Multi-CDN setup: Use Cloudflare as primary, but have AWS CloudFront or Akamai as backup
- Multi-DNS setup: Use Cloudflare DNS with Route 53 or Google Cloud DNS as secondary
- Multi-hosting: Distribute load across multiple hosting providers
- Geographic distribution: Host in multiple regions to survive regional outages
Technical Deep Dive: What Happened During the 2025 Outages
Understanding the technical details helps you appreciate the complexity and risks:
November 18: The Configuration File Cascade
The November 18 outage demonstrated how a single configuration file can cause global failure:
- Initial trigger: Bot Management configuration file exceeded size limits
- Cascade effect: Proxy processes crashed globally when they tried to load the oversized file
- Downstream impact: Workers KV degraded, affecting Access and Dashboard
- Recovery: Patch to Workers KV bypassed core proxy, reducing error rates
- Timeline: Issue identified at 11:31, investigation at 11:32, normal operations at 17:06
December 5: The WAF Rule Testing Failure
The December 5 outage showed how a corner case can cause system-wide failure:
- Initial trigger: WAF rule testing tool disabled to address saturation
- Failure mode: Logic error in corner case led to null pointer exceptions
- Impact: 500 HTTP errors served across 28% of traffic
- Compounding factor: Debugging systems consumed CPU, increasing latency
- Recovery: Configuration rollback restored service within 25 minutes
Common Patterns in Both Outages
- Configuration changes: Both caused by internal configuration, not external attacks
- Cascade failures: Single point of failure caused system-wide impact
- Testing gaps: Changes weren't properly tested before deployment
- Recovery time: Rollback procedures worked, but detection took time
Industry-Wide Implications
The 2025 Cloudflare outages highlight broader internet infrastructure risks:
The Centralization Problem
The internet is increasingly dependent on a few large providers:
- Cloudflare: 20% of internet traffic
- AWS: 32% of cloud infrastructure
- Google Cloud: 10% of cloud infrastructure
- Microsoft Azure: 23% of cloud infrastructure
This concentration creates systemic risk. When one provider fails, millions of sites go offline.
The Interdependency Problem
Many services depend on multiple providers, creating cascading failures:
- Sites using Cloudflare CDN + AWS hosting
- Services using Cloudflare DNS + Google Cloud
- Applications depending on multiple infrastructure providers
When one provider fails, it can trigger failures in dependent services.
Best Practices for Infrastructure Resilience
Building resilient infrastructure requires planning at every layer:
1. Design for Failure
- Assume every service will fail at some point
- Build redundancy into your architecture
- Test failover procedures regularly
- Monitor all critical dependencies
2. Implement Graceful Degradation
- Design systems that work with reduced functionality
- Serve content from origin when CDN fails
- Use cached content when live content unavailable
- Provide fallback services for critical functions
3. Monitor Everything
- Track uptime for all critical services
- Monitor performance metrics
- Set up alerts for anomalies
- Review logs regularly
4. Have Incident Response Plans
- Document failover procedures
- Train team on response protocols
- Test procedures regularly
- Communicate with users during incidents
Frequently Asked Questions
How often do Cloudflare outages occur?
Cloudflare outages are relatively rare but can be severe when they occur. In 2025, Cloudflare experienced three significant disruptions within four months (September, November 18, and December 5), which is unusual. Typical frequency: Major outages occur a few times per year. 2025 pattern: Three major outages in four months suggests systemic issues. Impact: Even rare outages can be devastating due to Cloudflare's scale (20% of internet traffic). Prevention: Don't rely solely on Cloudflare. Implement redundancy and failover mechanisms. Our maintenance plans include multi-provider redundancy to minimize impact from any single provider's outages.
Can I use Cloudflare and still have redundancy?
Yes, you can use Cloudflare while maintaining redundancy: DNS redundancy: Use Cloudflare as primary DNS, but configure secondary DNS with Route 53, Google Cloud DNS, or another provider. CDN redundancy: Use Cloudflare as primary CDN, but have AWS CloudFront or Akamai as backup. Security redundancy: Use Cloudflare WAF, but maintain server-level security. Hosting redundancy: Don't rely solely on Cloudflare for hosting. Best practice: Use Cloudflare for its benefits, but always have alternatives ready. Our infrastructure recommendations include multi-provider setups that maintain redundancy while leveraging Cloudflare's advantages.
What should I do if Cloudflare goes down while I'm using it?
Immediate response steps: 1. Verify the outage: Check Cloudflare status page and Downdetector. 2. Activate failover: Switch DNS to backup provider if possible. 3. Serve from origin: Bypass CDN and serve content directly from your server. 4. Monitor your site: Check if your site is accessible via direct IP or backup DNS. 5. Communicate: Inform users about the issue and expected resolution time. 6. Review impact: Assess which services are affected and prioritize recovery. Prevention: Having failover procedures documented and tested makes response faster. Our maintenance plans include automated failover and 24/7 monitoring to minimize impact.
Is it safe to use Cloudflare after these outages?
Cloudflare remains a reliable service despite the 2025 outages: Still reliable: Three outages in four months is unusual, but Cloudflare has a strong track record overall. Lessons learned: Cloudflare has committed to improving testing and rollback procedures. Risk mitigation: Use Cloudflare, but don't rely solely on it. Implement redundancy. Best practice: No single provider is 100% reliable. Always have backup plans. Our approach: We use Cloudflare for its benefits while maintaining redundancy through multiple providers. This gives you Cloudflare's advantages without single-point-of-failure risk.
How much does downtime cost businesses?
Downtime costs vary significantly by business type: E-commerce: €200-€2,000 per hour for small businesses, €10,000+ per hour for large sites. SaaS platforms: €500-€5,000 per hour depending on user base. Financial services: €10,000-€100,000+ per hour. Average small business: €600 per hour according to Gartner. Hidden costs: Lost customers, reputation damage, SEO impact, employee productivity loss. Cloudflare outage impact: The November 18 outage (3 hours) could cost a small e-commerce site €1,800-€6,000. Prevention ROI: Redundancy and monitoring cost far less than downtime. Our maintenance plans include redundancy and monitoring to prevent these costs.
What's the difference between a Cloudflare outage and a site being hacked?
Key differences: Cloudflare outage: Infrastructure failure affecting many sites simultaneously. Temporary. No security breach. Affects all Cloudflare customers. Site hack: Security breach affecting individual sites. Requires cleanup. Data may be compromised. Affects only compromised sites. Similarities: Both cause downtime. Both affect user experience. Both can damage reputation. Response: Outages require waiting for provider to fix. Hacks require immediate security response. Prevention: Redundancy prevents outage impact. Security measures prevent hacks. Our services address both: redundancy for outages, security for hacks.
Should I switch away from Cloudflare after these outages?
Not necessarily, but diversify: Cloudflare advantages: Excellent performance, strong security, global network, competitive pricing. Outage reality: All providers have outages. AWS, Google Cloud, and others also experience disruptions. Better approach: Use Cloudflare, but add redundancy. Don't rely solely on any single provider. Multi-provider strategy: Use Cloudflare as primary, but have backups ready. This gives you Cloudflare's benefits without single-point-of-failure risk. Our recommendation: Keep Cloudflare if it works for you, but implement redundancy. Our infrastructure consulting can help you design a resilient multi-provider setup.
Why We Write About Infrastructure Dependencies (And Why It Matters for Your Website)
You might be wondering: "Why is a website maintenance company writing about infrastructure dependencies? This isn't directly about WordPress or Joomla."
But it is directly related. Here's why:
When we give you a heads-up about critical security issues like Cloudflare outages, we're not just being helpful—we're protecting your privacy and saving all of us time. Here's the reality:
- Your infrastructure services passwords are valuable to hackers. If your CDN and hosting infrastructure gets compromised through an infrastructure vulnerability, attackers don't just steal your personal data—they steal your website passwords, your hosting credentials, your FTP access, and your database passwords. Suddenly, your website is compromised not because of a WordPress vulnerability, but because your CDN and hosting infrastructure was exploited.
- An educated client is easier to serve. When you understand security threats, we speak the same language. You know why we recommend certain security measures. You understand why we push for updates. You see the bigger picture—that website security isn't just about plugins and themes, it's about the entire digital ecosystem you operate in.
- Prevention saves everyone time. If you get hacked because of an infrastructure dependency failure, we have to clean up the mess. That takes time—your time dealing with the breach, our time cleaning and securing your site. By giving you a heads-up about critical issues like this, we're preventing problems before they happen. It's proactive maintenance, not reactive cleanup.
- Your security is our peace of mind. We sleep better knowing our clients are protected. When you're secure, your website is secure. When your website is secure, we don't have to spend hours cleaning up malware, restoring backups, or dealing with blacklist removals. Everyone wins.
This is why we write about infrastructure dependencies and other security issues that might seem "unrelated" to website maintenance. They're not unrelated—they're part of the same security ecosystem. Your infrastructure services is a gateway to your website. Your email is a gateway to your hosting account. Your operating system is the foundation everything runs on.
We're not just maintaining your website. We're maintaining your entire digital presence. And that starts with keeping you informed about threats that could compromise everything.
So when you see us writing about CDN outages or infrastructure failures, remember: we're protecting your website by protecting you. Because in the end, your security is our security. Your peace of mind is our peace of mind. And an educated client who understands the threats? That's a client we can serve better, faster, and more effectively.
