OpenClaw looks friendly. It promises an AI that actually does things: read your email, fetch files, run tasks across Discord, Telegram, and your machine. The problem is not the idea. The problem is that it is insecure by design, and the nightmare has already happened.
Last updated: February 5, 2026.
We have been following this project through its rebrands—warelay, clawdis, Clawdbot, Moltbot, and now OpenClaw. Security researchers have found tens of thousands of instances exposed on the public internet. Credentials stored in plaintext. An unauthenticated websocket that could leak your data if you clicked the wrong link. Malicious “skills” that exfiltrate session tokens to remote servers. Until the project gets serious about security, the safest move is not to use it.
What Is OpenClaw?
OpenClaw is a plug-and-play layer between a large language model and whatever you connect to it: email, Discord, Telegram, your filesystem, trading bots, web scraping. You give it access; you ask it to do things. It runs locally and serves a dashboard. It has no affiliation with Anthropic or any single model vendor—you can point it at different LLMs.
That sounds useful. The danger is that it removes the friction of scripting and APIs so that anyone can hook an LLM to everything they care about—including people who do not understand how much access they have just handed over. The Agents* are not in the code; they are in the design. One misconfiguration, one malicious skill, or one prompt injection can turn your helpful assistant into a backdoor.
Name Chaos and Attacker Opportunity
The project has rebranded repeatedly: warelay (November 2025), clawdis (December 2025), Clawdbot (January 2026), then Moltbot after Anthropic requested a name change, and finally OpenClaw. Each transition left behind old repos, package names, and search results. Attackers have used those abandoned names to publish fake updates and malicious packages that look official. If you search for Clawdbot or Moltbot today, you may land on something that is not the real project.
Thousands of Instances Exposed
Researchers have been scanning the internet for OpenClaw (and earlier Clawdbot/Moltbot) instances. Early reports in January 2026 found over 1,100 exposed control panels. By early February 2026, one report put the number of publicly accessible OpenClaw servers at over 21,000. Many were left open by users who did not realize that the default setup is not safe for the public internet.
OpenClaw often has shell command access and bridges personal and work accounts. An attacker who finds an exposed instance can grab auth tokens, read email, pull files from cloud storage, and run code on the host. In effect, the agent becomes a backdoor that the user installed and welcomed.

Critical Vulnerabilities
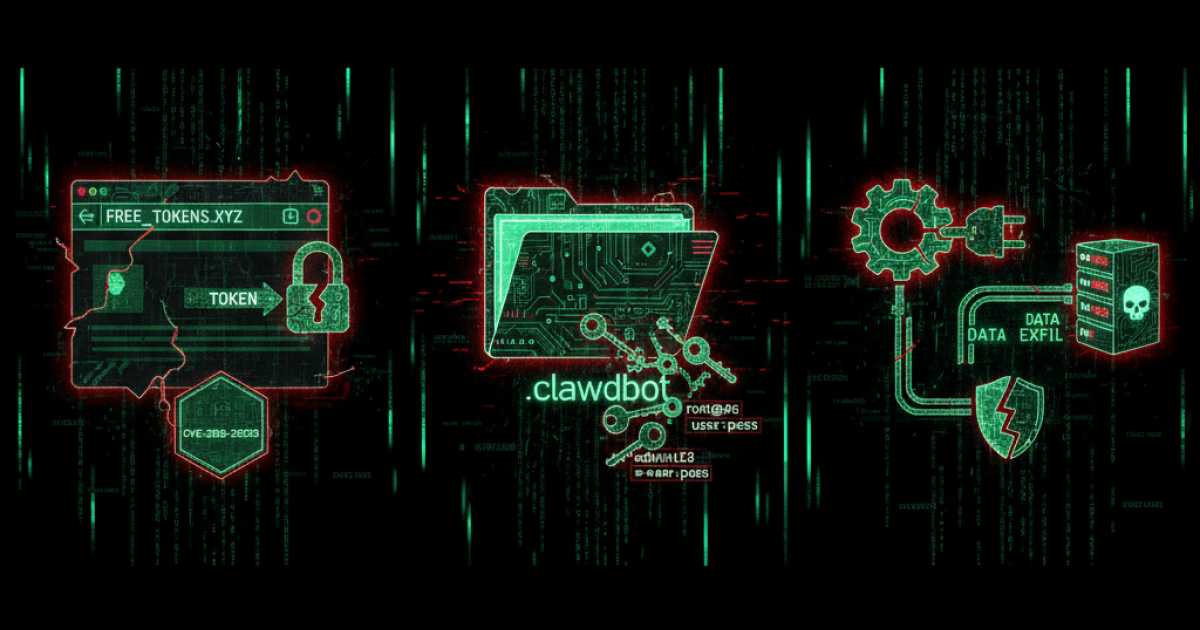
Unauthenticated Websocket (CVE-2026-25253)
One of the most dangerous flaws was an unauthenticated websocket (CVE-2026-25253) that accepted any input. With the default configuration, if you had OpenClaw running and visited a malicious webpage, that page’s JavaScript could connect to your local OpenClaw service, steal the auth token, and send commands—no click beyond loading the page. Your data could be leaked or your system abused without you doing anything except browsing. The fix arrived after the exploit was already public.
Credentials in Plaintext
API keys, login credentials, and tokens were stored in plain text under a ~/.clawdbot directory (and similar paths under later names). Deleted keys were still present in .bak files. Infostealers such as RedLine have been documented targeting these folders. In our experience, when a tool stores credentials in plaintext and exposes a control plane to the internet, compromise is a matter of when, not if. One compromise of your machine hands an attacker everything the agent can access.
Malicious Skills
OpenClaw uses “skills”—plugins or workflows that extend the agent. Malicious skills have been shared online; in one experiment a backdoor was inflated to become the most-downloaded skill (The Stack). Cisco’s threat research team demonstrated one example: a skill named “What Would Elon Do?” that used a hidden curl command to exfiltrate session tokens to a remote server and used prompt injection so the agent would run the attack without asking the user. That skill was manipulated to rank number one in discovery.
Optional Security
The project’s own documentation states that there is no “perfectly secure” setup. Authentication on the web dashboard is something users must turn on manually. Firewalls and secure tunnels are up to the user to configure. When Ox Security (a security research team) highlighted serious vulnerabilities to the creator, Peter Steinberger, the reported response was that it was a tech preview and a hobby, and that once it was production-ready or commercial, he would be happy to look into vulnerabilities. That is not reassuring when thousands of users are already running it with broad access to their data.
Who Gets Hurt
Personal users risk stolen session tokens, account takeovers, scams sent to their contacts, and loss of files from cloud storage. The agent can also make mistakes: users have reported it taking actions they did not ask for, such as sending email replies based on a misinterpreted prompt.
For businesses, a single employee running OpenClaw on a work machine and connecting work accounts can create an enterprise security nightmare. We’ve seen similar patterns with other “convenience-first” tools that get adopted before security is baked in. Traditional security tools may not flag it—the agent’s actions look like the user. A compromised instance can enable credential theft and ransomware inside the network while appearing as normal user activity. Many companies have banned tools like this for that reason.

What You Should Do
Do not use OpenClaw unless you are confident you can lock it down and vet every skill and integration. If you have been running it exposed: assume credentials are compromised. Rotate all API keys, OAuth tokens, and bot tokens. Restrict the interface to localhost or a tight IP whitelist and follow any hardening guidance from the project.
If you want an AI that can act on your behalf, prefer setups that separate the control plane from the data plane—for example, designating exactly what the LLM can and cannot access—so that one prompt or one plugin cannot hand over everything. The same principles apply to your website: minimize what you expose, use least privilege, and keep credentials and dependencies updated. We apply these practices in our security audits and maintenance plans so you can focus on real life* while we help guard the Matrix*.
For more on AI and security risks, see Clawdbot and Moltbot security risks and ChatGPT conversations harvested and sold.
Frequently Asked Questions
What is OpenClaw, and how is it related to Clawdbot and Moltbot?
OpenClaw is the current name of the same project that launched as warelay, then clawdis, then Clawdbot, then Moltbot after a rebrand request from Anthropic. It is a local AI agent that connects LLMs to your email, messaging apps, files, and other services. Only the name and branding have changed; the security concerns apply to all versions.
How many OpenClaw instances were exposed online?
Reports have varied by date. In January 2026, researchers reported over 1,100 exposed Clawdbot/Moltbot instances. By early February 2026, one report cited over 21,000 publicly accessible OpenClaw servers. Exact numbers depend on how and when scans were done; the point is that large numbers of instances have been left reachable on the internet without proper access controls.
What was CVE-2026-25253?
It was an unauthenticated websocket (CVE-2026-25253) in OpenClaw (under its earlier names) that accepted any input. With default settings, visiting a malicious website could allow that site’s JavaScript to connect to your local OpenClaw service, steal the auth token, and issue commands—leading to data theft or system abuse without further user action. The fix was released after the exploit was already public.
Are malicious OpenClaw skills real?
Yes. Researchers have documented malicious skills that exfiltrate session tokens to remote servers. Cisco’s team demonstrated one called “What Would Elon Do?” that used a hidden curl command and prompt injection to run data exfiltration without the user’s consent. Such skills have been shared and can be ranked to appear at the top in discovery.
Should I use OpenClaw at all?
Until the project adopts robust security practices—and many experts recommend waiting—the safest choice is not to use it. If you do use it, run it in an isolated environment, scope every key to minimum permissions, enable authentication and network hardening, and vet every skill and integration. The creator has stated it is not for non-technical users.
How does this relate to securing my WordPress or Joomla site?
Same principles: minimize attack surface, do not expose admin or API interfaces to the whole internet, use least privilege, and keep credentials and software updated. We help site owners do this through our security audits and maintenance plans.
